Remote Administration Tools are seemed to be the lowest of the low in mafia lore. It is a squealer that puts the very survival of the organization in danger. When it comes to protecting businesses from cyber threats, he needs to take a leaf out of the mafia’s book and handle RAT. You can try the NanoCore RAT download that comes in version v1.2.2.0 by Alcatraz on GitHub.
This is one of the sophisticated Remote Access Trojan which is used to create a backdoor to get administrative control over the victim’s device.
About NanoCore and its Origin

Taylor Huddleston, also known as Aeonhacks in 2016, admitted that he developed, marketed, and distributed this on the dark web from 2012-2016. He got arrested and jailed for 3 years in federal prison for aiding computer intrusions but without any luck still did not stop or slow down its spread. Security hackers kept his creation alive and kicking by releasing various versions. Its backend functions are very close to how njRAT works.
This high-risk RAT provides the attacker with all the details on the device name and operating system. The information is used for different malicious activities like:
- Hijacking webcam and microphone.
- Manipulating private files.
- Stealing credentials and much more.
It comes with base plug-ins that expand the performance capability of malware, inciting certain attacks. Over the years it has gone through many versions.
How NanoCore RAT operates

Mostly, they are designed for a certain kind of attack. However, it allows hackers to do anything they want over the infected device once they gain control.
Back in 2015, targeted emails were sent to energy companies in the Middle East and Asia by spoofing the email addresses of a South Korean oil company. With this was a malicious RFT file that dropped this Trojan.
A sequence of events shows how this was executed, putting the victim’s Office 365 and other data at risk. See the table below:
| Popular NanoCore Infection Techniques | How the Infection Happens |
| Email and Document Phishing | An email with a malicious RFT file is sent to the victim’s Outlook. |
| Payload malicious links | The user clicks on it and Trojan is uploaded on his device without detection. |
| Compromising email accounts | The keyloggers steal credentials of Office 365 to gain access to financial information and other critical data. |
| Ransomware injection | The information is then moved to servers owned by the security thieves. Victims are then asked to pay for the stolen data from Office 365. |
Important tip: Keep Office 365 administration credentials and data protected from cyber-criminals.
NanoCore Infection and Spreading Features
It is delivered by malicious email attachments such as MS Office documents but with advanced spam filters, criminals are forced to get creative, and one can bet that they are leaving no stone unturned.
Microsoft Office Products
These files are used to threaten actors to spread it. It comes with a distinct delivery method as the infection method takes place over many stages before the final payload is executed. You won’t believe that even email gate-away scanners cannot cut through the different layered approaches.
ZIP File Payload
Different zip file structures can bypass secured email gateways. One file shall payload it whereas the rest are decoys that ensure such content goes without notice.
ISO File
ISO files larger in files are difficult to scan, plus opening one is as simple as double-clicking on the file. This specific convenience increases the chances of victims clicking on such an attachment.
NanoCore Released v1.2.2.0
A new version of this infamous RAT, NanoCore version 1.2.2 has resurfaced on the dark web. For $25 a special kit is being sold with a free release. As it comes at a lower price it allows even a broken criminal to launch effective attacks.
This kit has:
- Plug-ins.
- The capability of reverse proxy connection.
- Remote surveillance with desktops, audio feeds, and webcam.
- 24/7 support.
The worst thing is that it is difficult to detect as most of the actions it performs are similar to other operations, making it look benign to most teams. Moreover, it is also used to carry out precise operations that do not resemble malware techniques, in the essence of pulling light from the eyes of all the IT administrators.
As a result, the businesses bleed money due to security issues, data loss, hardware damage, and long hours of unplanned downtime.
RELATED READ: Download Sentry MBA Configuration Files.
How To Stay Safe from NanoCore
- We need to educate our employees on best practices regarding security, which would help them stay alarmed against phishing scams.
- Do not rely only on the judgment of employees.
- Have a good backup and recovery system to protect a business when things go wrong.
- With spanning one can adopt a robust approach when dealing with RATs, it detection system ensures that IT administrators are given a clear insight into the backup health of the business. It alerts all the admins by flagging them through emails in case any issues are identified in the files. With this, they take the required actions to control the threat before it causes some major damage.
Analyzing NanoCore RAT components
Main components:
- ufj=ked
- exe
- jpg
Script file ufj=ked carries commented garbage code. Most of the code has comments disregarded by an interpreter. After cleaning this, the script file size came down to 7kb from 203kb.
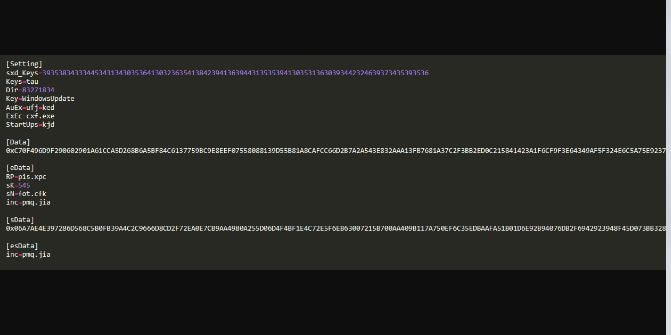
Following is de-obfuscated code in this script:
The third file is a configuration used by a script that carries a second AutoIT Script and a loader; this is also riddled with garbage values that need cleaning. The following image shows how it looks after cleaning.
Cxf.exe is a copy of Autoit.exe interpreter which runs a malicious Autoit script ufj=ked. When we go back to code ufj=ked and understand how it works, we can see that it is checking for the existing Avast AV process avastui.exe. After this, it finds the configuration file qnb.jpg and gets values sK and sN.
If the values are empty then the script terminates. If not, then it reads data between (sData) and (esDate) and gets the value to process the decoder function and execute the script. During this, a random file is written to the same directory with data from the configuration file. The new one is also an obfuscated AutoIT script, which also sets attributes of the file in the current directory to “read-only and hidden”. This one is familiar to others in older attacks.
NanoCore RAT Download (Latest) 2024 – Top Remote Administration Tool
This was all you needed to know about NanoCore Download and how it operates and infects. Various security companies also named This remote access tool malware of the month due to its infamous spree. It has unfortunately not been kept updated by its creator “Alcatraz” on GitHub but the current one works just as fine as before.
Build: v1.2.2.0.
Download NanoCore Free (Latest Version)