
Today when we buy smartphones we have our focus mainly on the material quality, the number of cameras it has, or the design whereas cybersecurity experts say that our focus needs to be on the security of the device and privacy of your data, which we 100% agree with. Below we have 10 great smartphones that are unhackable and untraceable for those who need such a level of protection.
We can say that mobile security is the actual problem therefore some of the manufacturers available to users are concerned about protecting the information stored on their devices.
Even popular phones are vulnerable to hacking therefore we must at least buy a safer device to save ourselves from all the thefts. This also includes iOS and Android, no platform is perfect.
10 Best Unhackable and Untraceable Phones for Ultimate Security
Blackberry DTEK50 – A trustworthy choice

Get this to protect your security at a reasonable price. This for sure is Blackberry’s return to the market.
As these are mostly used by law enforcement agencies, politicians, entrepreneurs, and activists but other people can buy and use them as well and keep in mind that some features are limited in favor of privacy.
Silent Circle Blackphone v2 – Stealth and Private

Get this to isolate all your conversations and be sure no intruder intercepts your communication. The device comes fully encrypted therefore no party shall hear anything including calls, messages, location, files and much more.
Finney U1 – Swiss-made
Swiss-based Sirin Labs developed this. It operated with military-grade blockchain technology at the software and hardware level. Moreover, the professionals say that it comes with an internet-free Bitcoin wallet which is ideal for cryptocurrency investors.
Bittium Tough Mobile 2 – Encryption Empire
A secure device that is designed for those who demand high security, the best thing about this is that it is not possible to hack it. Due to high standards, security agencies widely use it in more than 30 countries.
Bittium Tough Mobile

Though this is before version 2 it carries an advanced security feature that ensures that data is protected and cannot be in breach of security thefts.
IntactPhone R2 – Military Grade Security
This is an encrypted device that is best for military, police, and intelligence officers. This comes with military-grade ultra-encryption technology. This seems to be one of the best-secured phones with 6GB of RAM.
In this case, phone calls are encrypted, and service providers can’t decrypt messages or other communication even if they listen through any available hacking technology.
Its coverage is supported in Asia, Europe, the USA, Israel and LATAM.
ALSO CHECK: Top Linux Tablets that offer military-grade security.
Darkmatter Katim Phone
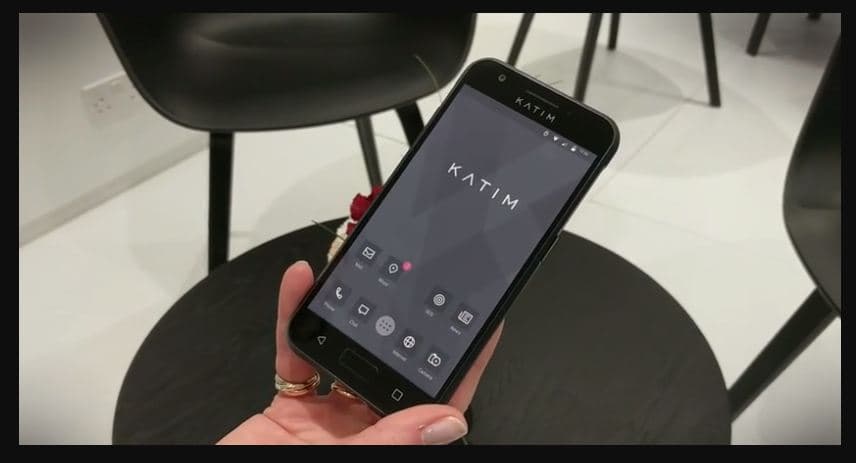
This is yet another secured smartphone device but there is less information about it. This is popular among many Asian-based clandestine operation agents as it is a well-encrypted mobile device. It has a good battery and is water-resistant. I would personally not recommend this because of the cheaper build quality and plastic back which are too common.
Intact Phone bond – Cyber Crime Protection
This is built from the ground up and is used to defend against all the cyber-crime. The best thing about this one is that it is an ideal phone that guarantees security and privacy online.
Its network coverage is being supported in; China, Japan, Canada, Israel, EMEA, APAC, Mexico, and the USA.
Intact Phone Arcane – Data Castle
Today top businessmen and women need to use such phones through which their data never leaks out. This is the best choice as its OS is embedded with IntactPhone Arcane which enables users to download and install such apps which are verified itself by the community security company. This is used to help prevent hacking as well as tracking.
This network coverage is being supported in Asia, Europe, Israel, the USA, and LATAM.
Purism Librem 5 – Strong from the OS
It is best known for its multiple features which provide control on software and protect all the sensitive data from common threats. It carries a kill switch for all pieces of hardware to turn off the sensors. These are reported to be found in cellular baseband, wifi, Bluetooth, and a microphone.
By default, it has trackers displayed and privacy protection enabled. Moreover, layered security protection and Linux operating system provides extra security and control over how information flows within the system like isolating apps from OS, and preventing data visibility from other apps which are running. Everything from security updates, bug fixes and privacy improvements ensures its security is on the mark and protects data all the time.
Blackphone PRIVY – Secure Communications

It carries such a design that helps protect high net worth users and company Executives from unscrupulous security thefts trying to grab their data and all personal information for some sort of financial gain.
Impressive security features are as follows:
- Carries end-to-end encryption.
- Reverse swipe.
- Cannot be tracked.
- Wiretap secure.
- Comes with a locked bootloader.
- Encrypted storage.
- Data separation sandbox.
These with many other features make it the best solution for all those users who want to have an Unhackable smartphone device.
ALSO CHECK: Best Linux Phones that can run Ubuntu.
OnePlus 8/8T, 9/9 Pro and 10 Pro
OnePlus has always been known as a brand you can customize for consumers. This is in a sense of installing your custom ROM (OS) on the device. Many are available, including the famous Cyanogen Mod, Lineage OS and Evolution X. You can install these on your mobile being well assured that your manufacturer won’t be spying on you as you will not have their OS on.
What these also allow you is to remove the default Google apps, these may be tracking you online or recording information, but not anymore. We highly recommend checking a OnePlus phone as they are also budget-friendly and won’t break your bank while giving you the best performance.
A 10-point Checklist To Keep Your Phone Secure
- Has an anti-virus been installed on your device?
- Do not install an application that asks for too many details.
- Make sure to download applications from trusted sites, still, if you need to app install an anti-virus protection application.
- If your phone gets lost or stolen then make sure to enable “Find my iPhone” or “find my Android” to lock or locate it.
- Use passwords, fingerprint locks or pin to protect your phone device.
- Update the device with the latest security patches is a must.
- Use VPNs if using public wifi.
- Regularly take phone backups.
- Use encryption apps.
- Do not open suspicious data like emails from unknown sources, any calls asking for personal details, and much more.
Importance of mobile security
When we talk about mobile security it means we refer to defending our phones from a wide range of cyber-attack vectors which pose a threat to privacy, network login, finances, credentials, and safety. Such security is used to protect us from all mobile security threats. This is your life as there are also various photos and videos that you would like to keep private, isn’t that correct?
The three MAJOR benefits are:
- Sensitive data is protected.
- Protection against malware.
- One is not vulnerable to any malware or other virus attacks.
Are you unhackable or untraceable?
There is no right or wrong answer. Every action you take on the web is recorded by your ISP and various other websites. However, using the best unhackable phone or untraceable phone by any of the above brands should also offer you encryption capabilities and privacy in stock form. You know the famous saying that something is better than nothing! Oh, and the most convenient part is that no satellite connection like in the movies is required.











Very curious to know if these also encrypt communication like text messages.
By default, I’m not sure they would unless you use an app like Telegram or Signal.
IMO everything is traceable, even with these phones.