When hacking is used to identify threats to a network or system then it is known as ethical hacking. It can be also referred to as intrusion testing, red teaming, and penetration testing, or even vulnerability scanning. But! How do you perform these? You can use any of the 12 best hacking tools for Windows 11 that are available as a free download to do this, there are open-source and beginner-friendly software on the list too!
To all those who do not know, hacking is a process in which we gain access to a system with the purpose of fraud, privacy invasion, data stealing, and much more by getting to know about its weaknesses. For example, they would try to break into the world’s most secure and unhackable phones which claim this to find a vulnerability.
Friendly reminder: The software mentioned below is not completely illegal if used ethically with permission. These are also great for beginners and you do not have to be a professional to get started.
Who Uses Hacking Tools – An Ethical Hacker
This is a person who is involved in hacking activities. These are of the following types:
- Phreaker.
- Hacktivist.
- Script kiddies.
- Grey hat.
- Cracker.
- The ethical hacker (white hat).
A security professional who uses his skills for defensive reasons is known as an ethical security theft. Now to strengthen their security they use their skills to find out all the vulnerabilities, compile them in the form of a document and the recommended ways to rectify them.
All the companies and organizations that provide users with online services to those connected to the net need to perform penetration testing by this. Now those who are new need to know that penetration testing is another name for ethical hacking but the difference is that it can be performed manually or via an automatic tool.
These users work as information security experts and try to seek the security of a system, network, or even applications. They are able to point out all the weak points and then provide suggestions to strengthen security.
This programming language includes SQL, PHP, Ruby, Python, Perl, Bash, C, C++, VBScript, Java, Visual Basic, HTML, JavaScript, and C Sharp.
Top 6 Hacking Certifications
These are as followed:
- CREST.
- OSCP.
- GIAC.
- CEH.
- CISA.
- Comptia Pentest+.
12 Best Free Hacking Tools For Windows 11 Used by Hackers

Netsparker – A Black Hat Hacker special

This one is an efficient tool that is used to mimic security theft moves to identify vulnerabilities like SQL injection and cross-site scripting in web apps and web APIs.
The best thing is you do not need to manually verify identified vulnerabilities once the scan is done and waste a lot of time as it can verify identified vulnerabilities proving they are real and not false positive.
Acunetix – Find XSS and SQL Injection Vulnerabilities
This is fully automated and able to detect as well as report more than 4500 web app vulnerabilities including all the variants of XSS and SQL injection/
It provides support to JavaScript, HTML5 and single-page apps thus allowing auditing of complex and unauthenticated apps.
It carries an advanced vulnerability management feature that prioritizes risks based on data through a single view and integrates scanners’ results into other platforms and tools.
Nmap – Free Security and Network Scanning
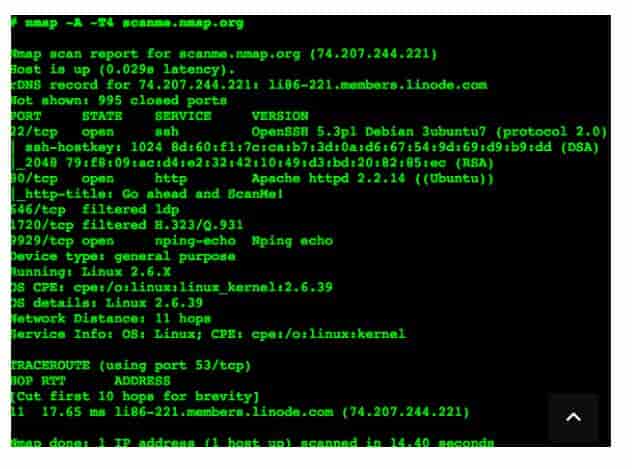
This is an all-in-one security scanner, port scanner and network exploration tool. It comes in free and is open source.
Cross-platform is supported and can be used to manage service upgrade schedules, network inventory, and monitor host and service uptime. The best thing is that it can work for both single hosts and large networks. It can provide binary packages for Mac OS X, Linux and Windows.
What you can do with it:
- It can transfer data, redirection and is a debugging tool (Ncat).
- GUI and results viewer (Nping).
- Packer generation.
- The response analysis tool (Nping).
- It is able to scan results comparing utility (Ndiff).
Using RAW IP packets it can determine the following:
- Hosts are available on the network.
- Operating systems.
- Services offered by tools available.
- They use packet filters.
- Other characteristics.
It is easy to use and works fast plus it seemed to be the best scanning tool.
RECOMMENDED: NanoCore RAT by alcatraz3222 (Official Download).
Metasploit Framework – #1 PenTesting Platform
These are open-source tools that can be downloaded for free. Its pro version is deemed to be a commercial product. For 24 days, we can give it a free trial. We can get to know about its pricing details by contacting the company.
This is used for penetration testing, developing and executing exploit code against remote machines. The best thing is that it provides support for cross-platform.
What you can do with it:
- Know about security vulnerabilities.
- Create security testing tools.
- Helps in IDS signature development.
- Helps a lot in penetration testing.
It is best to build evasion and anti-forensic tools.
Aircrack-Ng – Hacking Wireless Networks
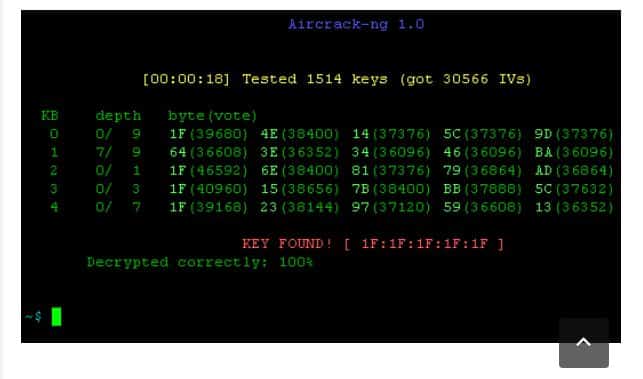
This is another option on the list that comes in free and provides users with various tools to evaluate wifi security.
For wifi security, it focuses on monitoring, attacking, testing, and cracking. It supports free BSD, OS X, Linus, Windows, NetBSD, Solaris, OpenBSD, and eComStation 2.
What you can do with it:
- Crack WPA2-PSK and for this uses dictionary attacks.
- Crack WEP keys and use FMS attack, PTW attack and dictionary attacks.
- Check wifi cards and driver capabilities.
- Provides support to export data to text files.
- It has its focus on replay attacks, fake access points, de-authentication and much more.
The best thing about this is that it supports any wireless network interface controller.
Wireshark – Sniffing Network Traffic
This tool comes in free and is basically a packet analyzer that can perform a deep inspection of different protocols.
It is able to provide support to cross-platform. With this users can export the output to various file formats such as XML, CSV, Plaintext and PostScript. With this, we can apply coloring rules to the packet list so that analysis can be easy and quick.
What you can do with it:
- Decompress gzip files on the fly.
- Decrypt various protocols such as ISAKMP, IPsec and SSL or TLS.
- Perform live capture and offline analysis.
- With this users can browse captured network data by using GUI or TTY-mode TShark utility.
Ettercap – Perform MiTM attacks
This option can provide support for cross-platform. With this, we can create customized plug-ing. It can perform sniffing of HTTP SSL-secured data even with the proxy connection.
What you can do with it:
- Network analysis.
- Host analysis.
- Content filtering.
- Protocols active and passive dissection.
- Live connections sniffing.
With this, we can create customized plug-ins, which is great.
TOP READ: Google Dorks For Live IP Cameras and Credit Card Details.
Burp Suite – Penetration Testing and Vulnerability Scans
If we talk about price then these are 3 in number. For free you can download the community edition. The Enterprise edition starts at $3999 per year whereas the professional edition starts at $399 per user yearly.
It carries a web vulnerability scanner and advanced and essential manual tools.
It provides users with many advanced features and carries three editions; community, enterprise and professional. It provides manual tools with community tools whereas paid versions provide many features such as the web vulnerability scanner.
What you can do with it:
- CI integration.
- Schedule and repeat scan.
- Scans 100% generic vulnerabilities.
- It uses OAST which is an out-of-band technique.
- It provides users with a detailed custom advisory for reported vulnerabilities.
It is best for security testing,
John the Ripper – Password Cracking at its finest
If you are looking for a tool for password cracking then we suggest this one. It is used on DOS, Windows, and Open VMS. It comes in free and is open-source. Moreover, it is also used to detect weal UNIX passwords. You can use big wordlists such as the famous Rockyou.txt password list to perform brute force on targets of your choice to force your way on a login screen.
What you can do with it:
- Carries customizable cracker.
- Provides users with different password crackers in one package.
- Performs dictionary attacks.
- Test different encrypted passwords.
It is quite fast in password cracking.
ALSO CHECK: 8 Best Search Engines For Privacy and Hacking.
Angry IP Scanner – Deep scan your network
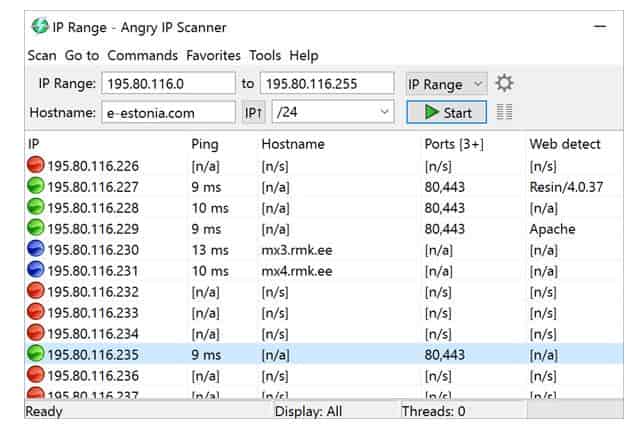
This one is used to scan IP addresses and ports. It can scan both on the local network and the internet. It provides support to Mac, Linux and Windows operating systems.
What you can do with it:
- Export results in different formats.
- A command-line interface tool.
- Extensible with many data fetchers.
Nikto – Test your Webserver
It is open-source and comes in free plus used to scan web browsers. With this, we can scan web servers for dangerous files, outdated versions and certain version-related problems. With this, we can save reports in XML, text file, NBE, HTML, and CSV file formats. Moreover, it can be used on a system that provides support to basic Perl installation. Use this on Windows, UNIX, Mac and Linux systems.
What you can do with it:
- Check servers for over 6700 dangerous files.
- Comes with full HTTP proxy support.
- It identifies installed software using favicons, headers and files.
- With this, we can scan the server for outdated server components.
It is great for penetration testing tools.
Maltego – Forensics and Intelligence use
Maltego CE is a community version that comes in free whereas Maltego Classic costs around $999, Maltego XL $1999. These two are designed for the desktop. Server products like ITDS, CTAS and Comms start at $40000 and the best thing is that this price includes training as well.
This is used for link analysis and data mining and supports Linux, Windows and Mac operating systems.
What you can do with it:
- This data is represented on node-based graph patterns.
- XL version works with larger graphs.
- Provides graphical pictures and tells regarding network weak points as well as abnormalities.
ALSO CHECK: Vulnerable Websites List For 2024.
12 Hacking Tools for Windows (All Compared)
| Hacking Tool | OS Support | Use Case |
|---|---|---|
| Netsparker | Windows and Cloud Based | Build a secure coding standard in your environment |
| Acunetix | Windows 10/11, Linux and Cloud | Scan your web based applications for any critical bugs |
| Nmap | Linux | Discover malicious and un-welcome hosts/devices on your network |
| Metasploit Framework | Windows 10/11, Mac and Cloud | Aim and scope vulnerabilities much better |
| Aircrack-ng | Linux and Mac | Wireless network security testing and hacking |
| Wireshark | Cross-platform and Windows | Scan the networks |
| Ettercap | Mainly Linux and Mac OS | Sniffing network packets and stopping man in the middle attacks |
| Burp Suite | Windows and Linux | Vulnerability testing for apps hosted in the cloud |
| John The Ripper | Linux | Cracking forgotten and weak passwords |
| Angry IP Scanner | Windows, Mac and Linux | Scan networks for malicious connections and hosts |
| Nikto | Linux | Scan any outdated software on your environment |
| Maltego | Apache, Microsoft IIS and Nginx | Scan your webservers for any weaknesses |
Conclusion: Best Hacking Tools for Windows 11
There is no one-size-fits-all all rule here. As you have seen above, you can pick various choices for your needs. This is where our list of the 12 best hacking tools to download free will help you increase your horizon for your ethical hacking career. They include Penetration testing, vulnerability scanning, network scanning and brute force capabilities. Choose wisely!











A great collection I’d say, especially in the ethical and unethical hacking software/tools category!