Today many people wonder which tools are used by security professionals or bug bounty hunters for finding different vulnerabilities on devices that are connected to the internet. Everyone uses certain tools normally but there are search engines that are designed for security researchers. This article focuses on the best Search Engines used by Hackers and other security personnel. These can help you with a vast amount of devices, domains and other addresses that could be open for attack and need attention.
Though many people think that a hacker is a bad entity, the reality is quite the opposite, as most of them are dedicated to investigating and finding security flaws so that later on the affected organizations and even themselves could provide a solution in this respect.
Top 8 Search Engines You Should Use as a Hacker
Shodan – Internet of Things Wonderland
This is a free web service that allows users to see which devices have access to the internet and if they carry any security flaws. It is ideal to see if there are some web cameras, smart TV, alarms, AC and other devices in a digital home that are connected to the internet and vulnerable to different kinds of attacks.
It is very popular among users and is the most used search engine as it provides a large amount of information and allows us to see in detail if there is any security issue in the device, or what information it carries about the public IP address.
Censys.io – The best search engine for internet devices (Top Pick)
This is a search tool where you can see attacks that are suffered by various systems and apps in real time. It also comes with a free domain search engine where you can see and access different information regarding domains like which ports and protocols are used, and which certificate is valid. It also comes with a certificate search engine where we can check if it is valid and which key is the last valid.
It carries an IPv4 address search engine; here you can find different relevant information plus the approximate location of the IP address. The best thing is that it comes with interesting payment options with which you can see how a detected security breach has been resolved. To have more information visit Censys.io.
Now, let’s see what kind of information it provides and how one can interact with it. It collects data from the system and sites through daily scans with ZGran and ZMap regarding IPv4 address space. At the end of this, we have regular snapshots of how systems and sites are configured. One can interact through:
- Downloading in “raw data” mode the databases.
- API for plug-in interactions.
- Search engine on the site.
The former are large JSON files and like in my Talk we downloaded files having more than 43 GB, representing all IPv4 machines with port 21 open and with a banner grabbing done on the machine.
We can get more information regarding the architecture on which it is mounted and its functions in the paper that has been published by its authors. Elastic Search, Google Datastore and Google BigQuery, another option which is mentioned above is downloading of raw data via compressed files that host JSON.
Just like Shodan, it carries different tools which add intelligence to the data collected like the possibility of discovering many tools to analyze information that has been collected previously.
This is an interesting source of information that provides various mechanisms to play with the information and build interesting things such as applying intelligence on data and crossing it with public exploits with the purpose of conquering the world. If you have responsibility for security in an organization, it is useful to see what any potential attacker may be collecting from the infrastructure.
Recently, they finished their series A funding from which the company raised $15.5 million. They have also said to raise the number of employees they have by 3X with only the top security talent.
Zoomeye – Open servers and ports at a glance
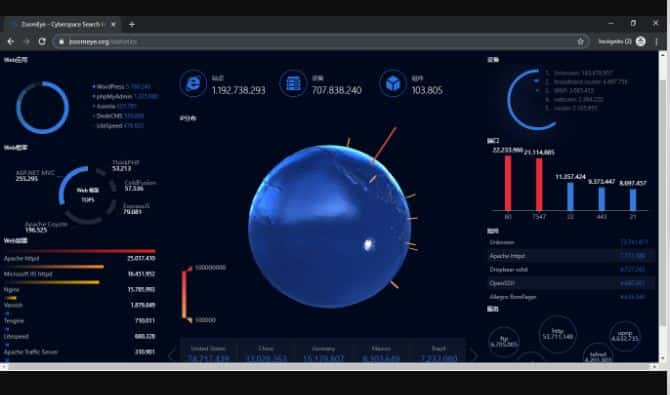
This one is similar to Greynose but was developed for the Chinese market. It carries a search engine where when we enter the IP address or any word then it shows us with information about it. As it is in Chinese we suggest that you use it with a translator as though the results shall be shown in English, however, some menus and data will not.
It comes with an interesting section known as “statistics”, where we are able to see different stats on the planets of all kinds, from countries, browsers, servers, protocols and much more.
GreyNoise – Background noise of the internet
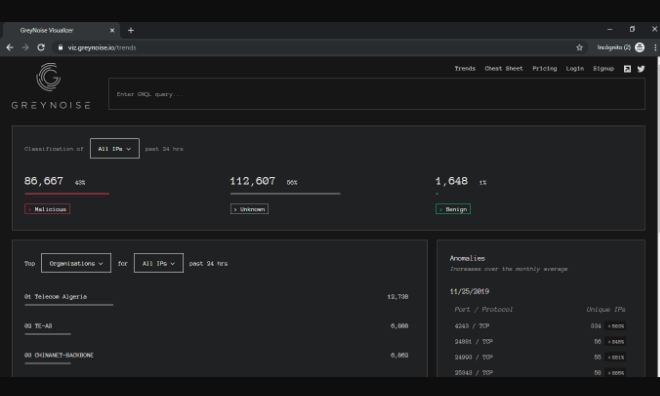
It comes with a search engine where you enter the IP address and search for words. Depending on what has been entered, it shows information regarding attacks, faults or malicious sites that it finds. It also has a section there in the lower right side of the search bar known as “explore trends” where we can see different stats which are updated in real-time like anomalies detected in various ports, malicious attacks and much more.
All this comes in free but if you wish to have more accurate information like IP lookup, more advanced queries or support then you need to buy payment options for organizations worth 2.999.
PublicWWW – Source Code Heaven
This is a web through which a search engine allows to search for HTML.JS and CSS code in any web page. It is simple to use and quite useful. Its operation is simple as well. Once we enter the site, we need to enter in the search box, the code which we desire to find out if it is on any site. Once there, click to the right in the bar where the code has been introduced, the button “search” and it shall show the results.
If we want to know which syntax we could enter in the search box then we need to click below where it says in blue “query syntax: RegEx, ccTLDs and much more” and we shall open a new page, with different ways in which to search the code.
Must Read: Top Vulnerable XSS and SQL Injection Testing Sites and Web Apps.
Wigle – A Map of Wireless Networks on the globe
This is a search engine for wireless networks by coordinates. To put in other words, when we enter it we find a map and to the right, we can enter latitude and longitude coordinates to reach some point on Earth. If we zoom we shall be able to find different hotspot networks which are available in the place. It also had wifi devices, Bluetooth as well as telecommunication antennas. It is very useful to know what surrounds us and if we have any network available nearby.
Recommended Tool: Sniff any PlayStation or Xbox IP Address using OctoSniff.
Hunter.io – Find any email address
This is a site that carries a search engine where we enter the name of the company and it shows us all the email addresses which have been filtered on that company. This site is beneficial if you want to find an email address. It has a simple operating system. First, we need to enter the site in the search box, the name of the company we wish to find out if any email address has been filtered. Once it has been introduced we need to click right in the bar where we have introduced the direction of the email, the button “find email addresses” or when we introduce the name of the company could appear in the searcher.
Once when you click on it and it does not find anything then the following message shall appear below the following search box:
Error: “This doesn’t look like a domain name”
Now if you find any results then you shall see email addresses found and next to the green icon if they are still active or yellow if you do not know or have any idea. Moreover, it also shows a downward error on the right side of every email address which informs us which site has found the email of the company which we are looking for and also tells us whether the place where we have found it is still active or not.
A new update has been released that allows you to also search academic email addresses which usually include .edu or .ac extensions.
OSINT Framework – The holy grail of data finding
This is a web in which through the use of different menus we can find links to various sites regarding the information on the category we are looking for. When we enter the site then we can find on the left side a series of sub-categories which we shall see next, where we try and follow different options according to what we want. In the end, it leads us to a series of results, if we click on them they shall open a new tab with a search engine that we have selected. Keep in mind that if we click on the blue ball then another sub-menu shall open however if it is white then the selected tab shall be open.
Must Read: What is njRAT and how you can use it on Kali Linux.
Closing Statement
Hacker search engines simply make it easier for bug bounty hunters, vulnerability researchers and other such individuals life easier. You can find millions of potentially vulnerable domains or IoT devices that can be exploited. Security researchers have started using this to their advantage to alert companies to make their defenses stronger. Our personal favorite is Censys because of its recent enterprise capability and funding series.